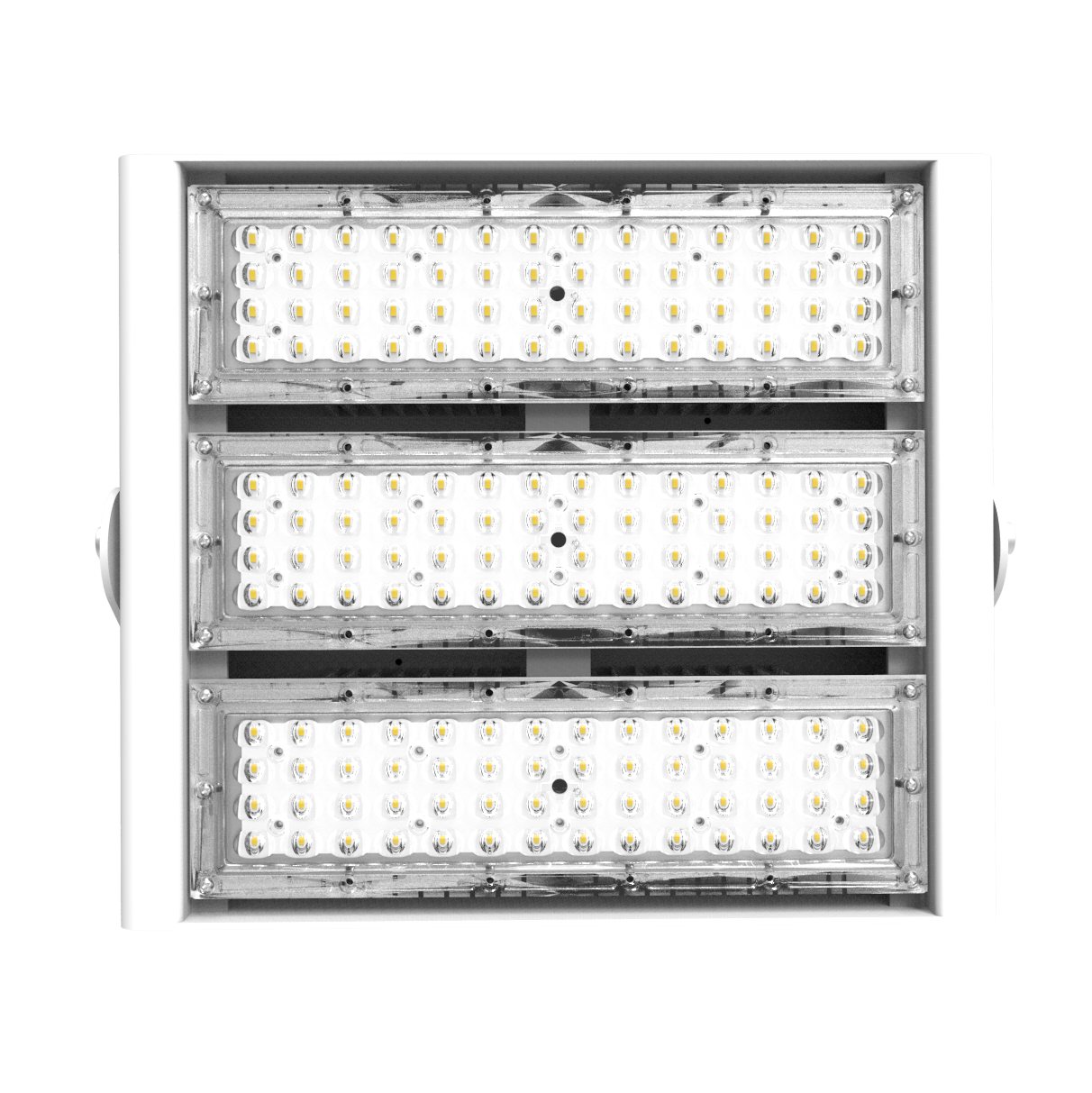
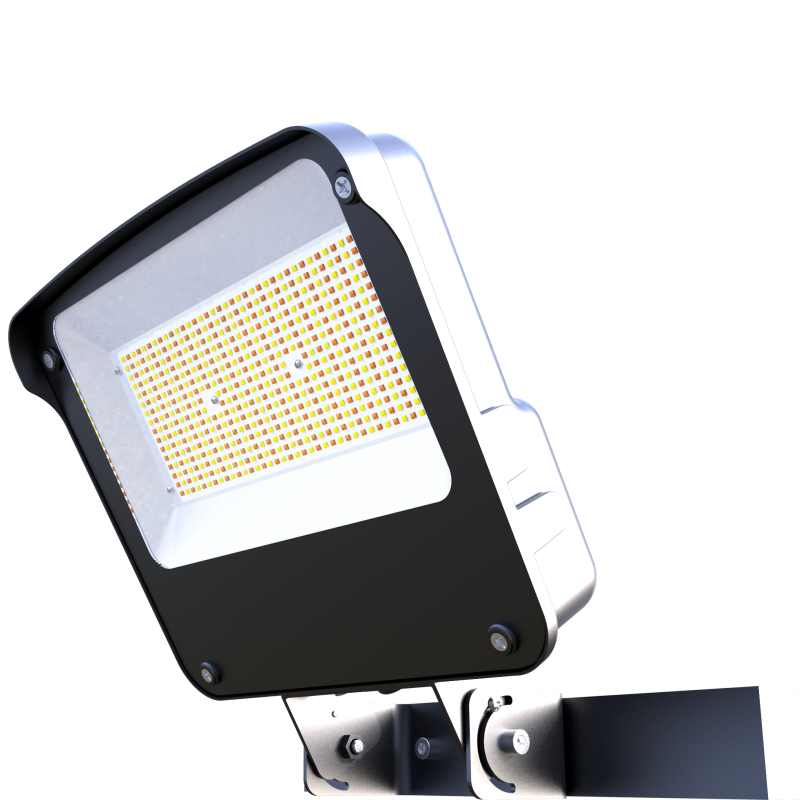
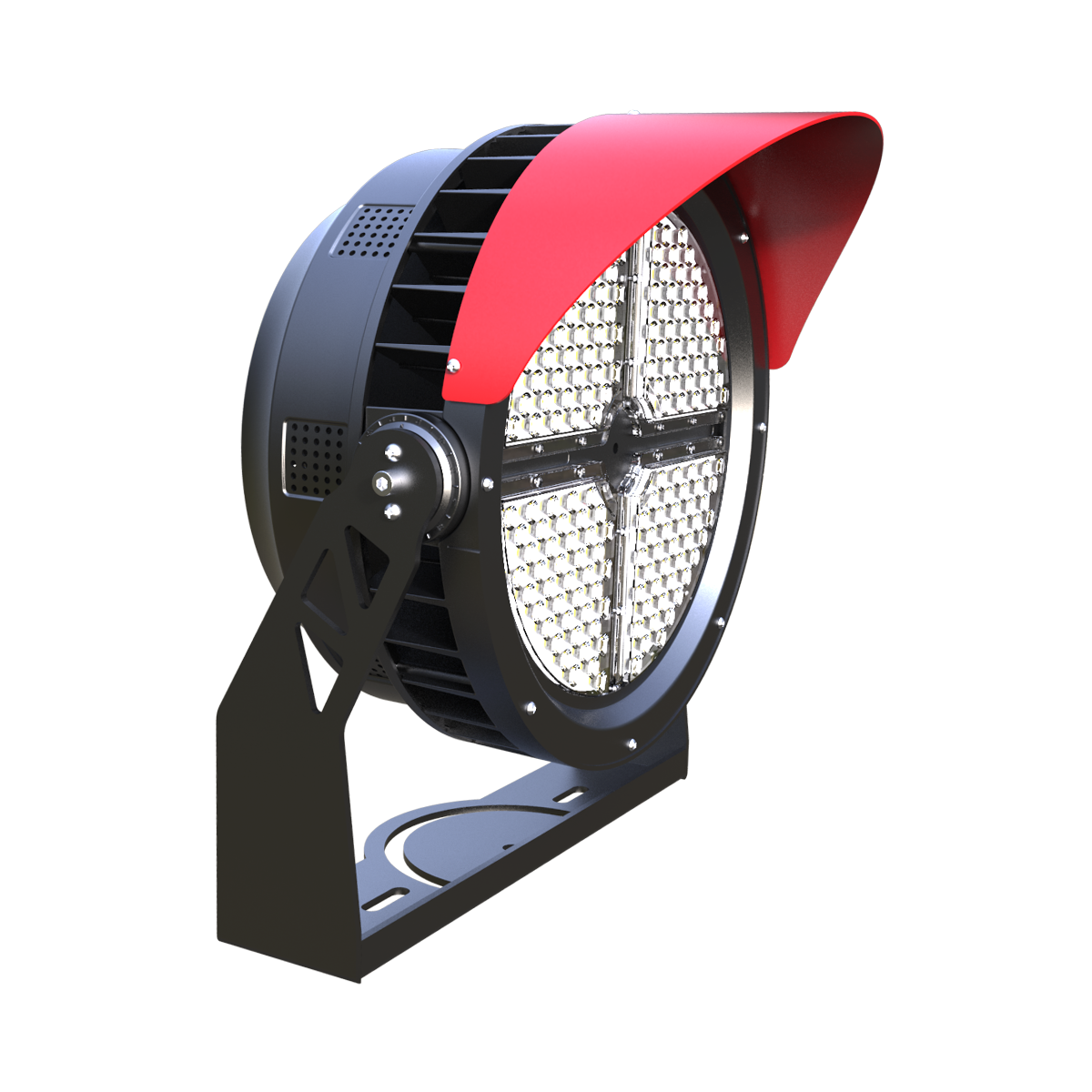
Top China Manufacturer of Security Flood Spotlights for Optimal Safety
When I think about enhancing security for outdoor spaces, Security Flood Spotlights come to mind as an essential solution. These powerful lights not only deter intruders but also provide peace of mind. Sourced directly from a top manufacturer in China, our spotlights are designed for durability and efficiency, making them suitable for various commercial settings. I love how easy they are to install and adjust, ensuring that every corner of a property is well-lit. The energy-efficient design helps in reducing costs while maintaining high visibility, allowing me to keep my operations running smoothly. If you're a B2B purchaser seeking reliable security lighting, these flood spotlights can be a game-changer for your business. With our commitment to quality and customer satisfaction, I’m confident you’ll find these products meet your needs perfectly. Let’s light up your security like never before!
Security Flood Spotlights Where Innovation Meets 2025 Your End-to-End Solution
In an era where technological advancements redefine industries, the security landscape is witnessing groundbreaking innovations, especially in the field of flood lighting. As we approach 2025, the integration of smart technology in security solutions provides an unparalleled end-to-end approach for enhancing safety and visibility. These advanced flood spotlights not only illuminate spaces but also incorporate cutting-edge features such as motion detection, energy efficiency, and remote monitoring, making them essential for modern security systems. Global procurement stakeholders are continuously searching for solutions that offer reliability and sustainability. The latest generation of flood spotlights seamlessly combines innovation with functionality, allowing users to customize their security needs while reducing operational costs. Whether for commercial installations or residential applications, these solutions are designed to adapt to diverse environments, providing peace of mind through superior visibility and intelligent features. As we move forward, embracing these state-of-the-art security flood lights will empower businesses and homeowners alike, ensuring safety while leveraging the latest technological innovations. The future of security is bright, and staying ahead of the curve by investing in comprehensive solutions will allow you to secure your assets effectively as we approach 2025 and beyond.
Security Flood Spotlights: Where Innovation Meets 2025 Your End-to-End Solution
| Feature | Description | Benefit | Implementation Timeframe |
|---|---|---|---|
| Cloud Security Monitoring | Continuous monitoring of cloud environments for threats. | Enhances threat detection and response time. | 3-6 months |
| AI-Powered Threat Analysis | Utilizes AI to analyze and predict security threats. | Reduces false positives and prioritizes threats. | 6-12 months |
| Automated Compliance Reporting | Automates the generation of compliance reports. | Saves time and ensures regulatory compliance. | 1-3 months |
| End-to-End Encryption | Encrypts data from source to destination. | Protects sensitive data during transmission. | 1-2 months |
Related Products
Security Flood Spotlights Application From Concept to Delivery
Top Selling Products
-

WhatsApp
-

E-mail
-

WeChat
Judy

-

Top